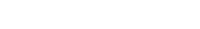Prolaborate and OKTA SAML Integration
Prerequisites
Your Prolaborate site should have a valid SSL Certificate.
If you don’t have an SSL Certificate, you can create a self-signed certificate yourself. Please get in touch with the Prolaborate team to know more about it.
Service Provider Configuration
To configure the Service Provider, click on Menu → SAML Settings.
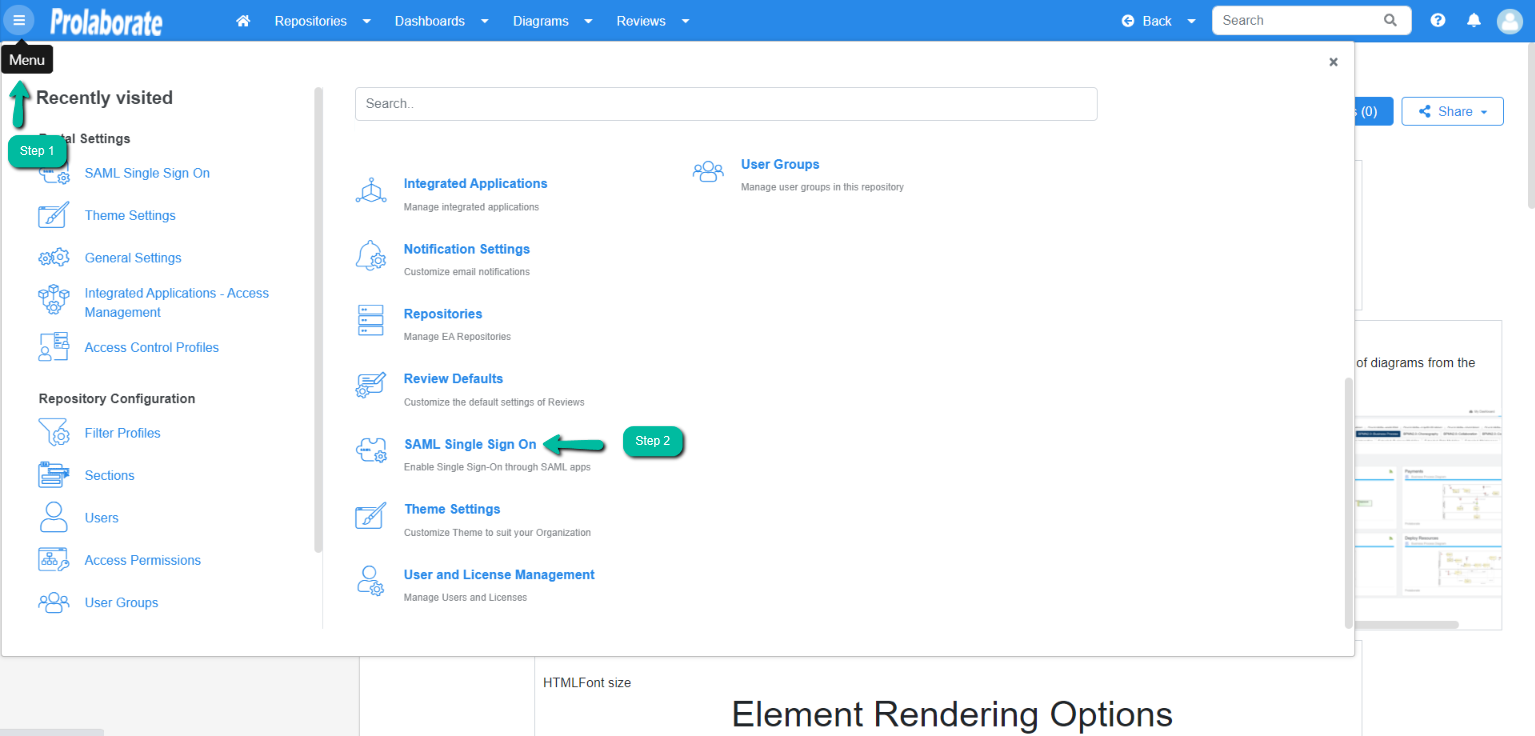
From the top of the page that opens, click on Enable SSO.
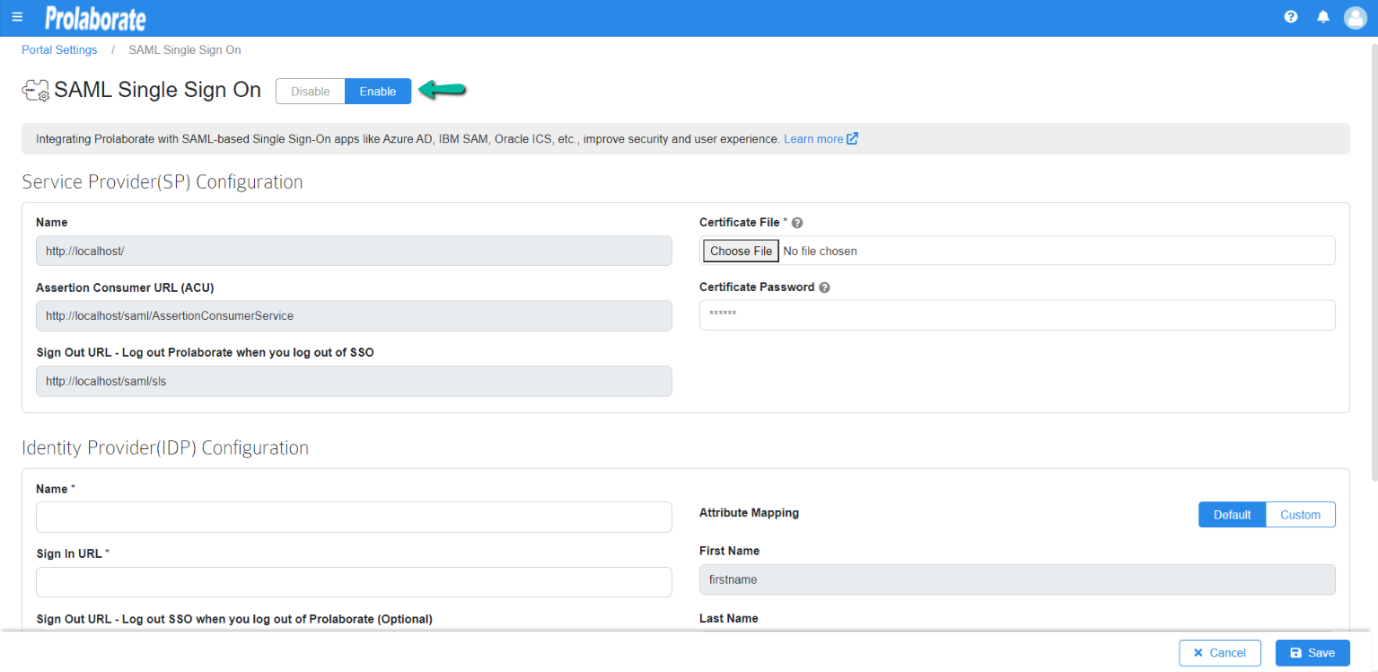
| Name | Name will be prefilled |
| Assertion Consumer URL | Assertion Consumer URL will be Prefilled |
| Certificate File | Choose the .pfx file of your SSL certificate |
| Certificate Password | Enter the Password of the .pfx file |
Configuring Prolaborate in Okta
The following sections will elaborate on the steps involved in setting up Prolaborate in Okta.
Create a new SAML Application
To create a SAML application, follow the below steps:
Log in to your Okta account as a user with administrative privileges. Click on the Admin button.
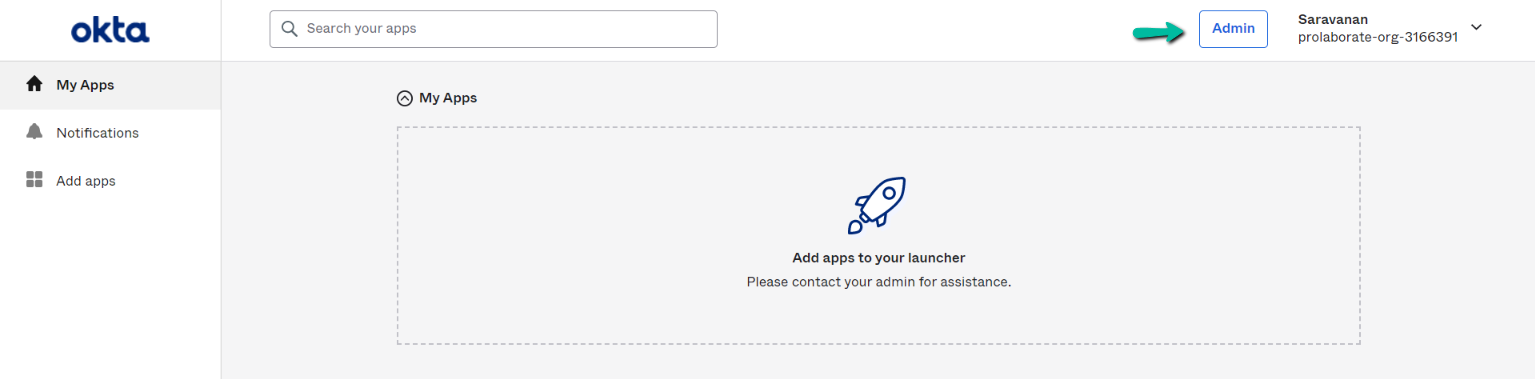
Click on the Applications tab.
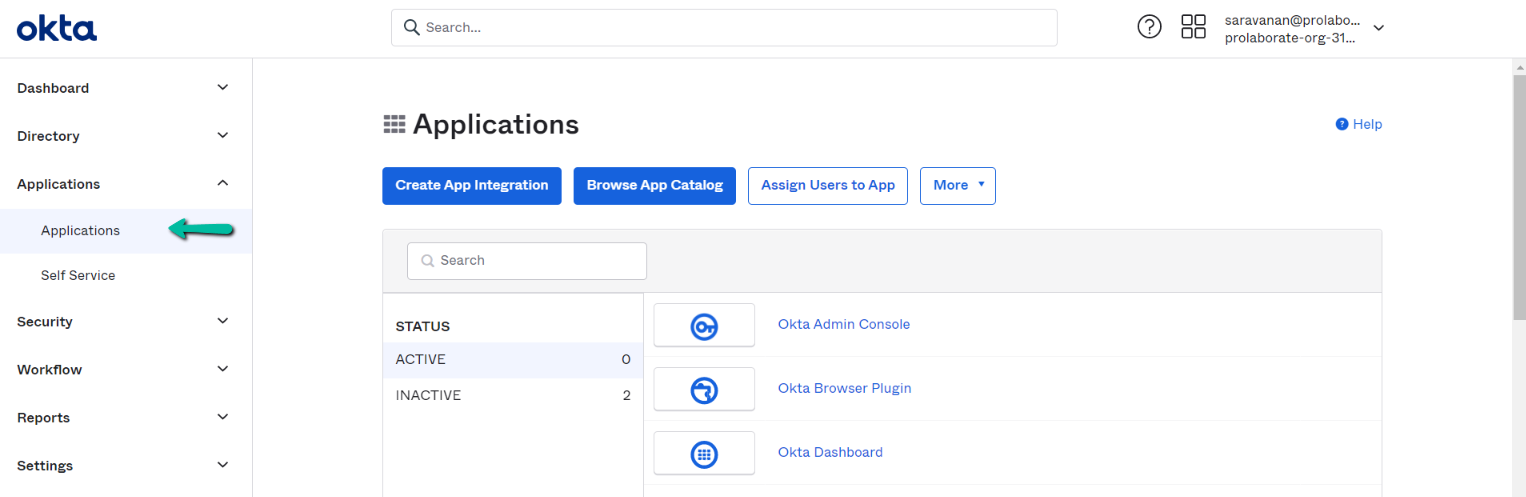
Click on Create App Integration button
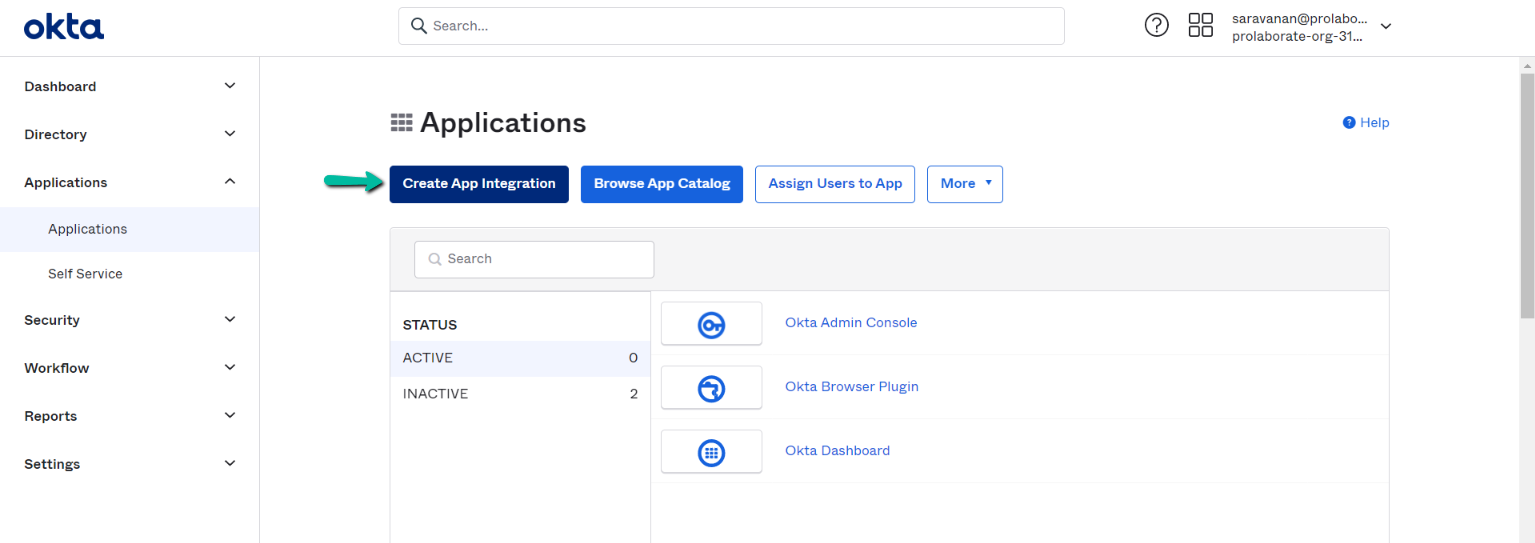
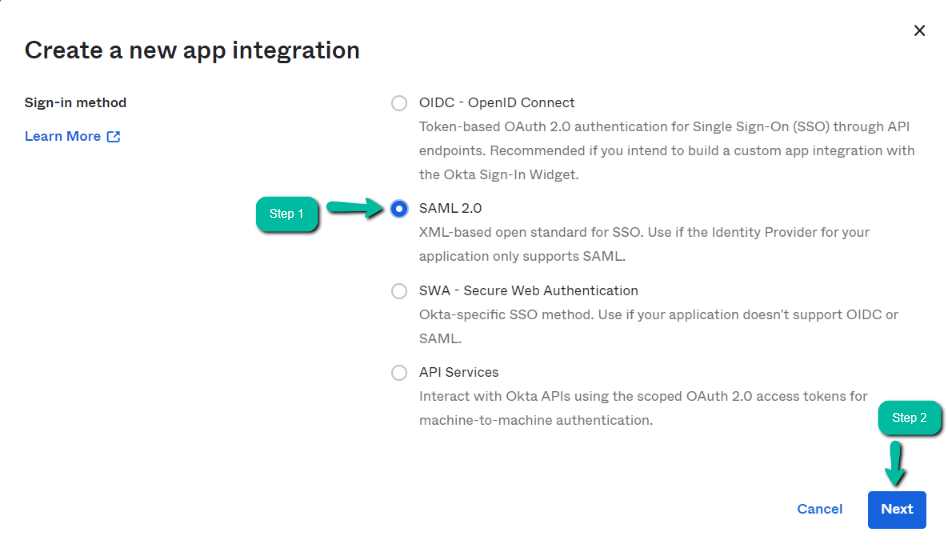
Select the Sign-in method as SAML 2.0 and click on the Next button.
General settings
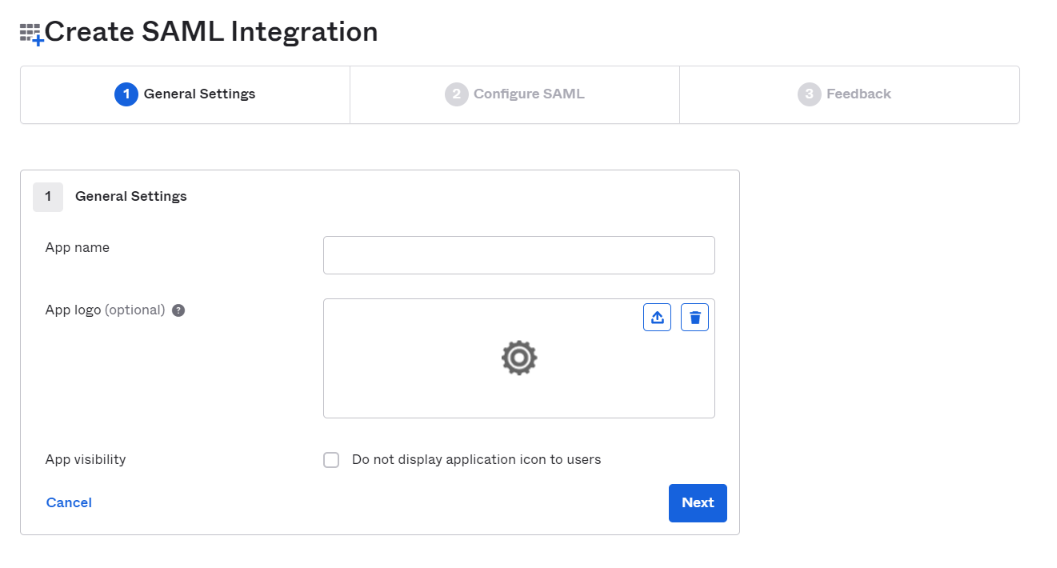
In step 1, fill General settings as per the instructions below and click on Next.
| App name | Enter your Application Name (say Prolaborate). |
| App logo (Optional) | Review the tool tips for details about the type of image you can use for your logo. |
| App visibility | You can leave these options unchecked. |
Configure SAML
In step 2, fill Section A – SAML Settings as per the instructions below.
| Single sign on URL | Fields from Prolaborate Service Provider configuration as stated above (In section Service provider Configuration). |
| Audience URI (SP Entity ID) | Fields from Prolaborate Service Provider configuration as stated above (In section Service provider Configuration). |
| Use this for Recipient URL and Destination URL | Select this box as the recipient and destination URL to be the same. |
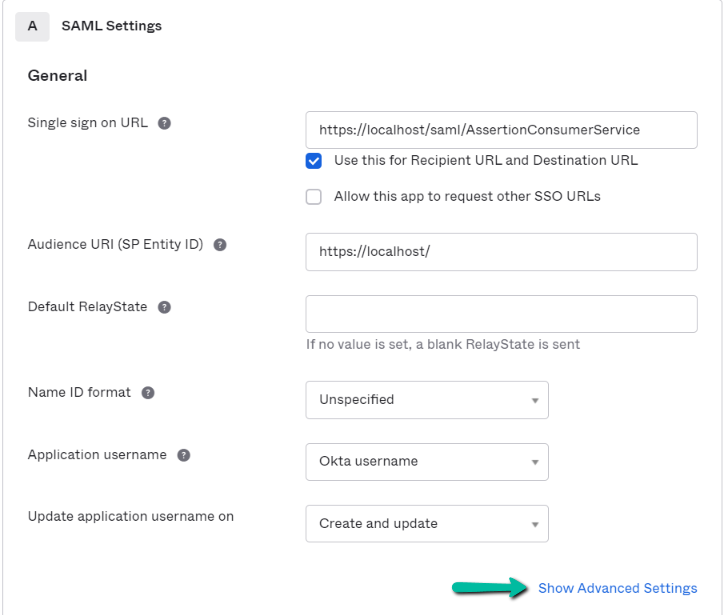
Click on Show Advanced Settings.
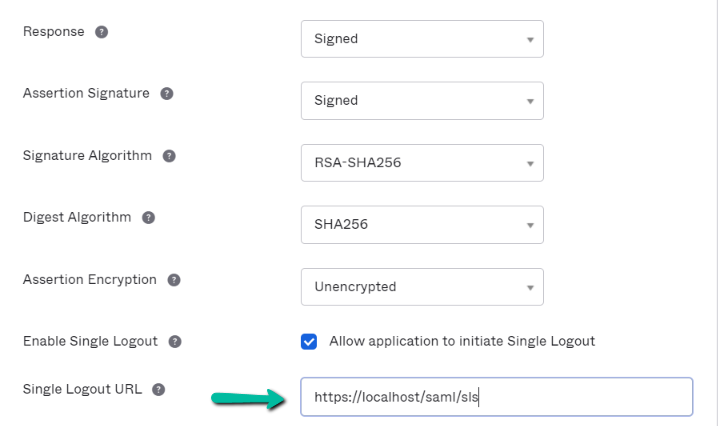
Check the Enable Single Logout to allow the application to initiate single logout.
| Single Logout URL | Get Name fields from Prolaborate Service Provider configuration as stated above (In section Service provider Configuration).For example, https://localhost/saml/sls |
| SP Issuer | Enter the URL from the Service Provider Name field from Prolaborate |
| Signature Certificate | Browse SSL certificate (.cer file) of Prolaborate instance and click on Upload Certificate |
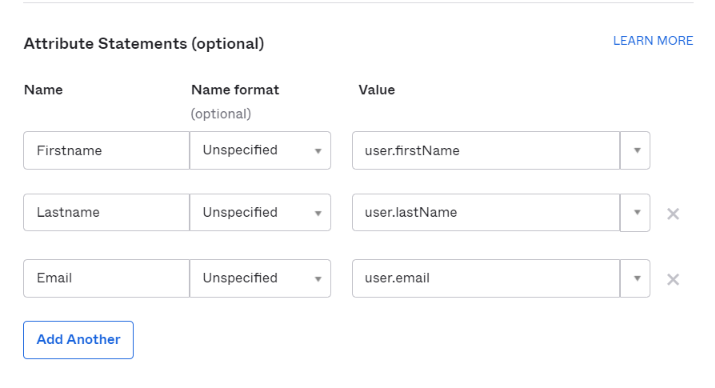
Attribute Statements should be configured as below:
| Attribute Name | Value |
|---|---|
| Firstname | user.firstName |
| Lastname | user.lastName |
| user.email |
You need not change any other settings
Section B is not needed for Prolaborate. You can just click on Next.
Feedback tab
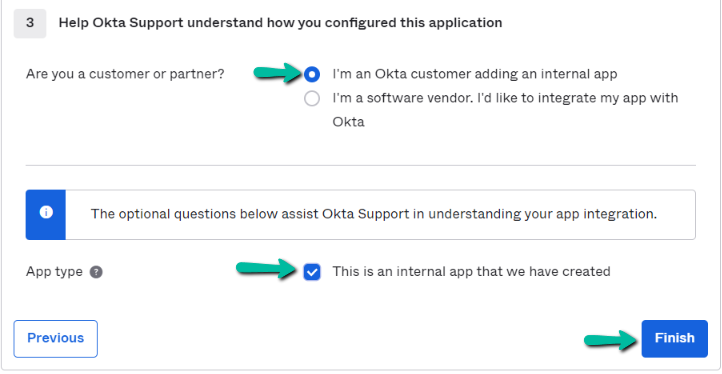
In Step 3, select I’m an Okta customer adding an internal app and This is an internal app that we have created, and Click Finish
Assign Users
In this section, we will assign the Okta users to the Prolaborate application. Click on the Assignments tab.
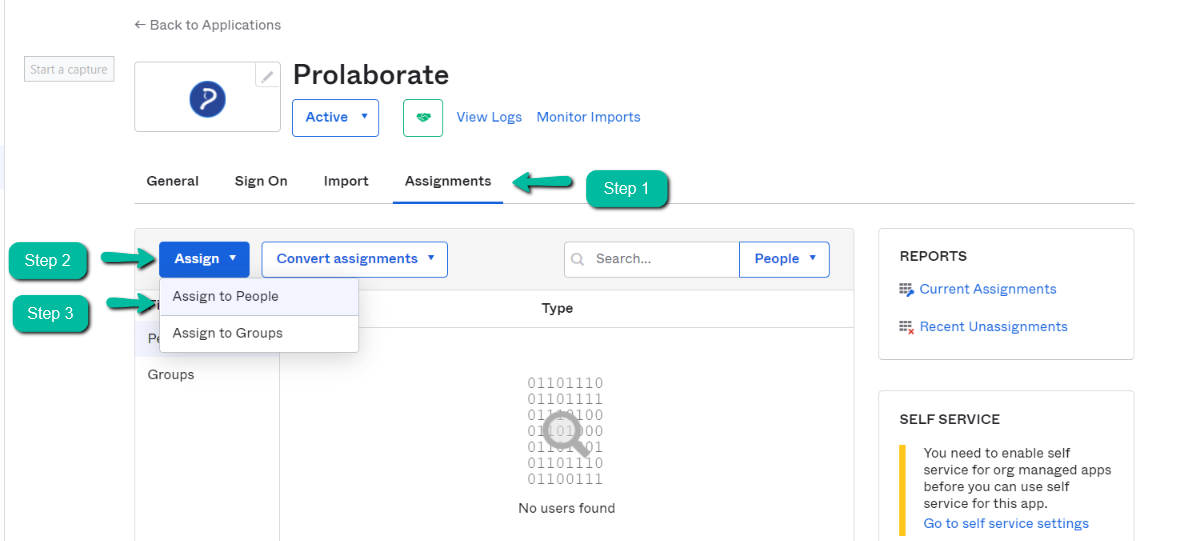
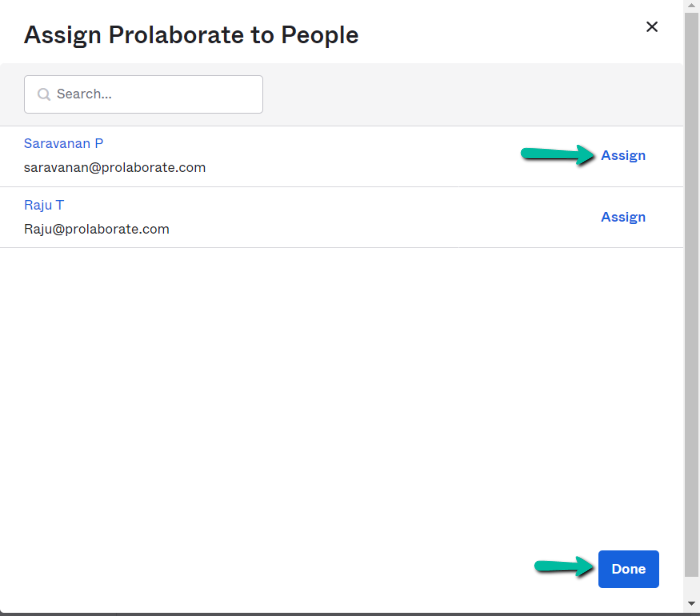
Click on Assign on the users to whom you want to give access to Prolaborate on Assign Prolaborate to People page.
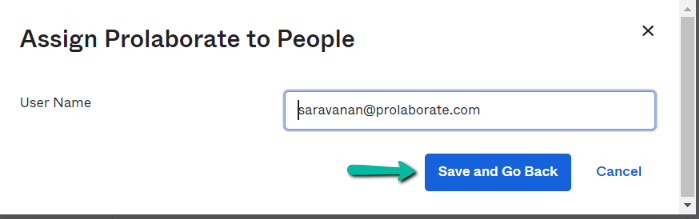
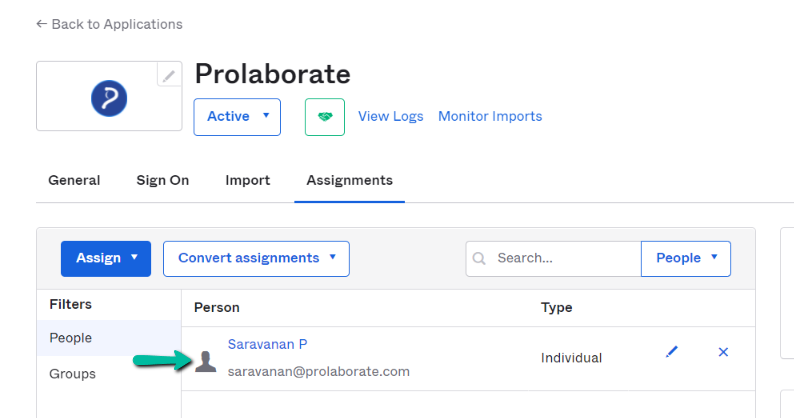
The users whom we have selected will now show up in the Assignment tab
Sign On Tab
In this section, we will configure the Identity provider to your Prolaborate. Click on the Sign On tab
Click on View Setup Instructions.
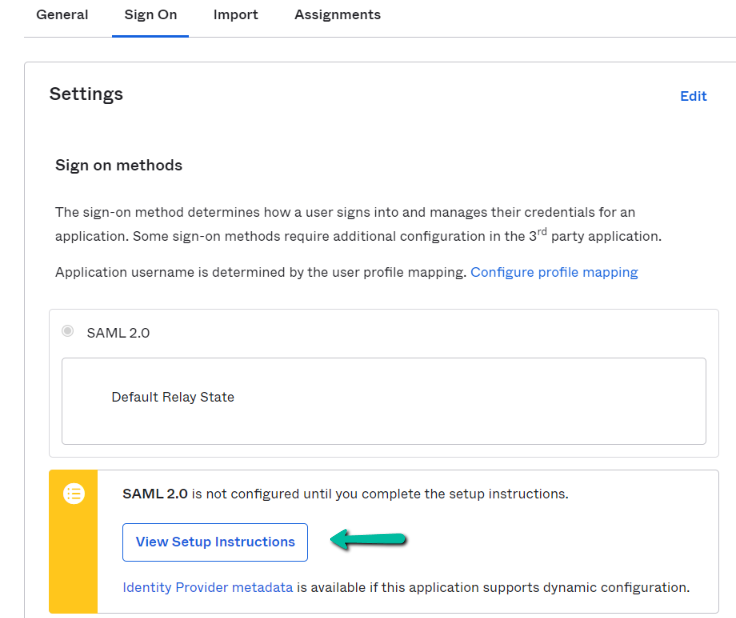
Identity Provider Configuration details will be shown in a new tab.
Identity Provider Configuration details will be shown in a new tab
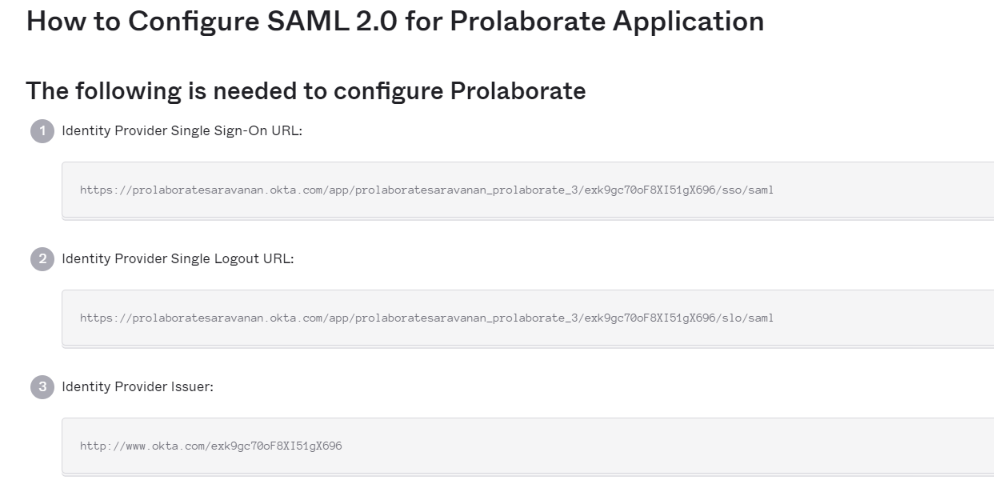
| Identity Provider Single Sign-On URL | Should be used as Sign In URL field in Prolaborate Identity Provider configuration |
| Identity Provider Single Logout URL | Used as Sign Out URL field in Prolaborate Identity Provider configuration. |
| Identity Provider Issuer | Used as Name field in Prolaborate Identity Provider configuration respectively. |
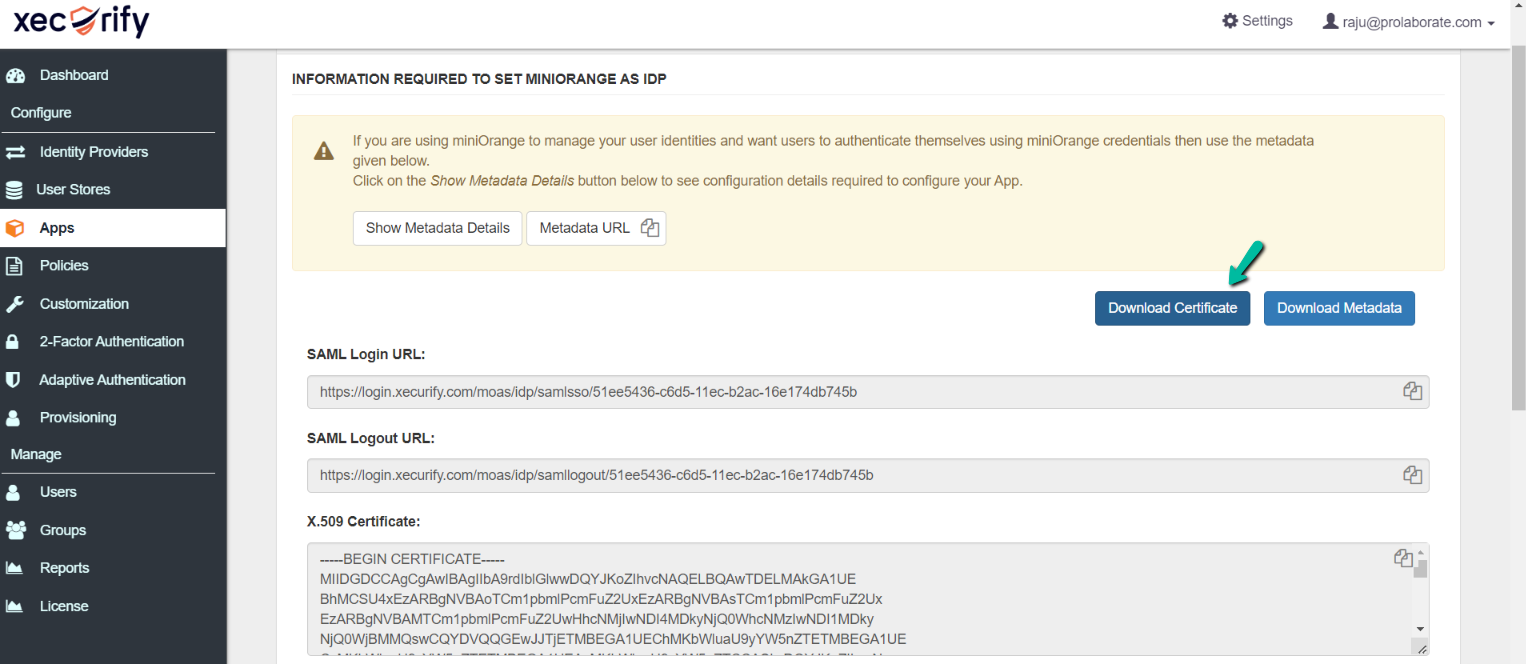
Click on Download Certificate to download the .cer file and it is used as the Certificate field in the Prolaborate Identity Provider configuration respectively.
Identity Provider Configuration
Go back to Prolaborate, and click on Menu → SAML Settings.
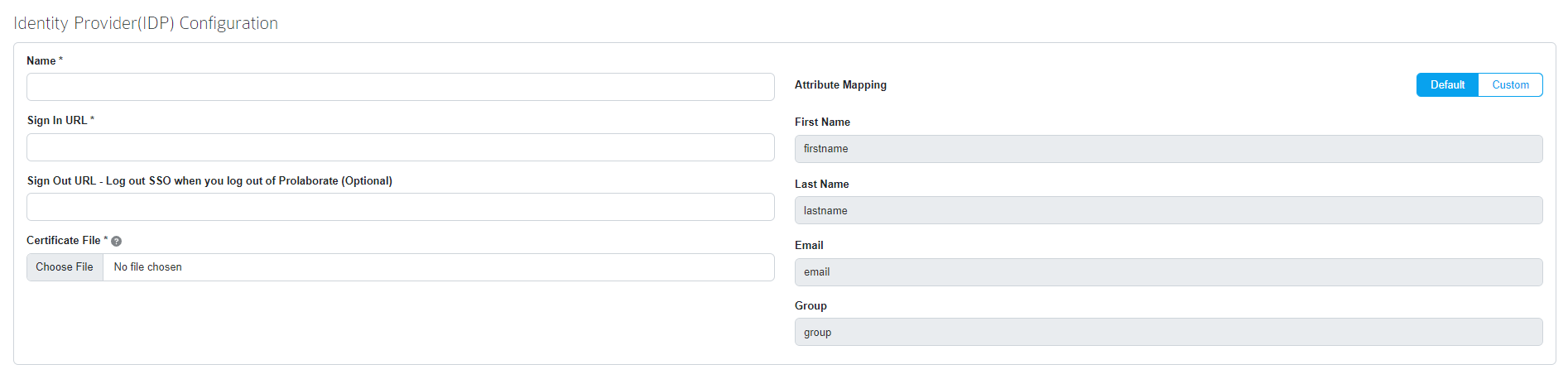
Fill the Identity Provider Configuration as per the instructions below:
| Identify Provider | Select Other |
|---|---|
| Name | Fill using Identity Provider Issuer URL availed from Okta configuration (Refer to the section Sign On Tab ). |
| Sign In URL | Fill using Identity Provider Single Sign-On URL availed from Okta configuration (Refer to the section Sign On Tab ). |
| Sign Out URL | Fill using Identity Provider Single Logout URL availed from Okta configuration (Refer to the section Sign On Tab ). |
| Certificate | Choose the .cer Certificate file from Okta Configuration (Refer to the section Sign On Tab ). |
Attribute Mappings
Change the Attribute mapping into the Custom Mode and fill the following values in the respective fields.
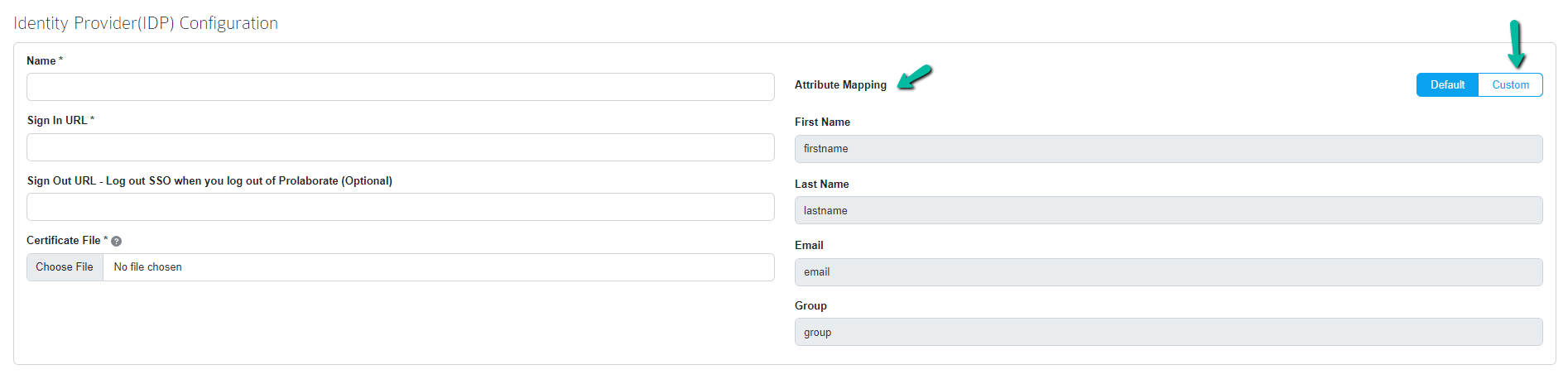
| Attributes Mappings | Claims |
|---|---|
| First Name | Firstname |
| Last Name | Lastname |
| EmailNote:Based on the claims, which is configured in SAML Application. Please choose the Email type. | |
| Group | Usergroup |
Default Access Control Profile
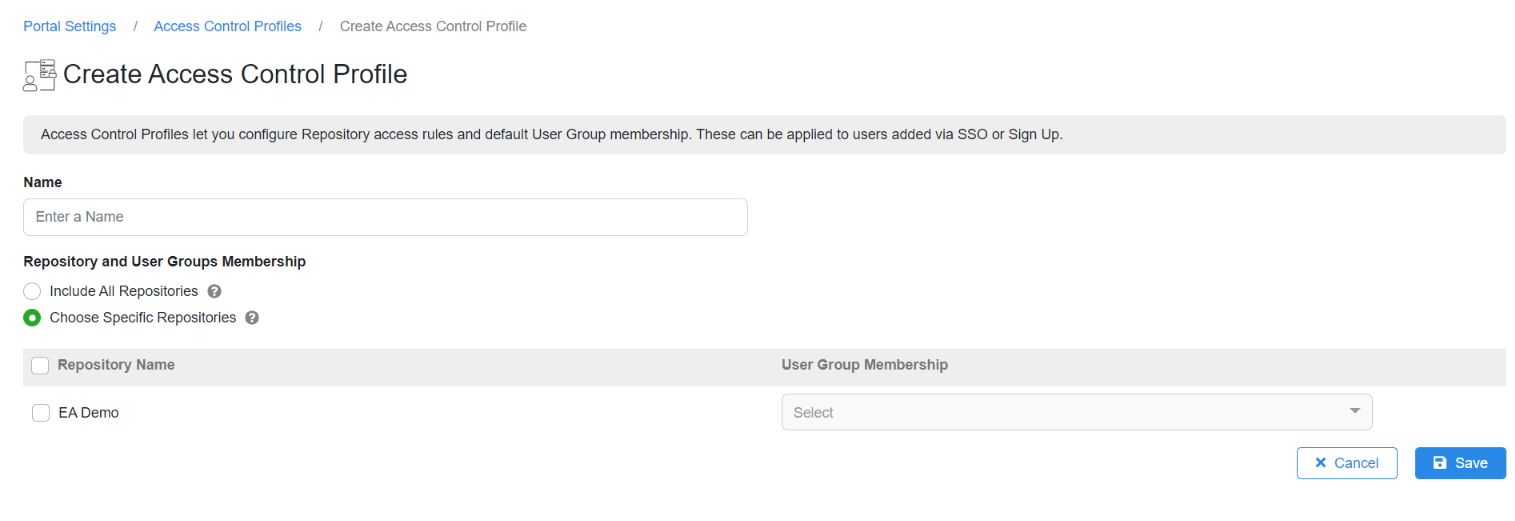
Click on Manage Profiles to create a new profile.
Click on Create Profile.
Give a name to the Profile and configure permissions.
This is the permission that will be provided to all the users logging into Prolaborate using their SSO credentials.
You can choose any one of the following options:
| Include all repositories | Any user logging in with their SSO credentials will be given access to all repositories |
| Choose Specific Repositories | Any user logging in with their SSO credentials will be added to the user groups you have specified after selecting the repositories |
Click Save.
Now, go back to the SAML Settings page.
Select the newly created profile and click Save.
Log in with Okta Credentials
Once the configuration is done, users will start to see a new button on the login page called Login with SSO.
When they click on Login with SSO,

They will be redirected to an URL as per configuration. They can then give their OKTA credentials to login to Prolaborate.
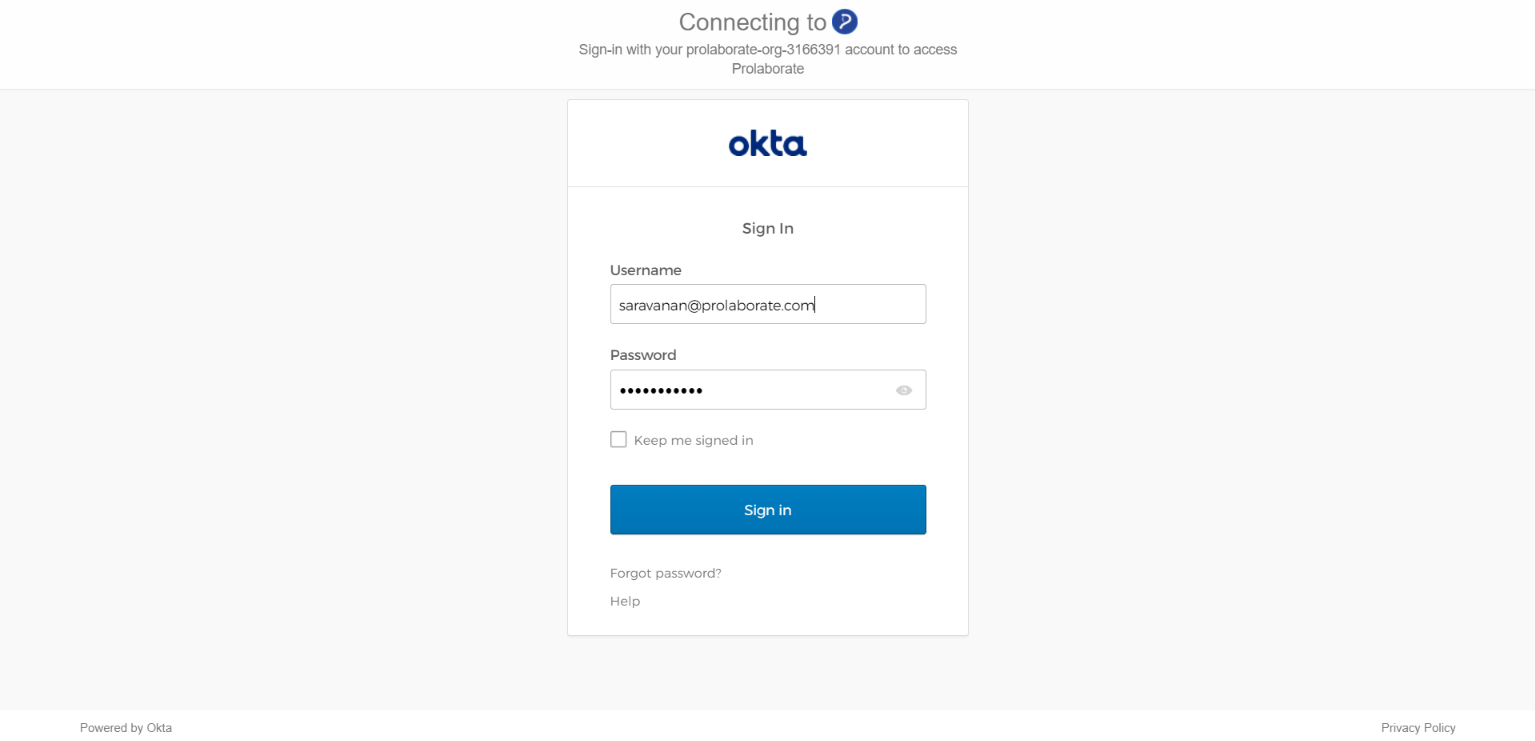
You will be redirected to Prolaborate successfully if the configuration is done right as said in the document.
If you’re experiencing challenges signing in using SSO, go at SAML Assertion Validation to debug the SAML configurations.
Note the Repositories you see will be based on Default Access Control Profile
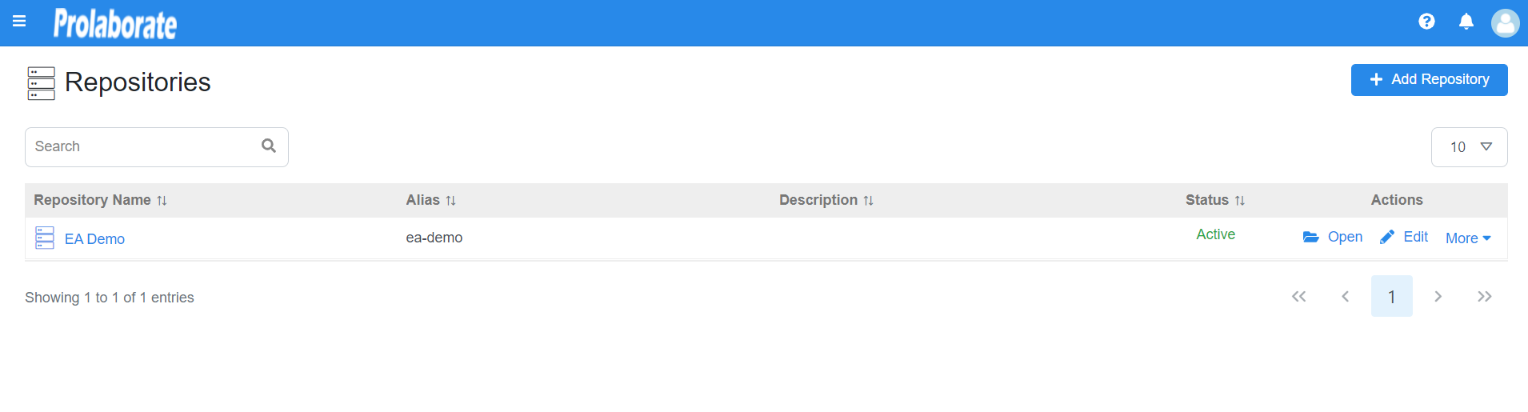
Please check the configuration if you are not logged in to Prolaborate.
Logging out from Prolaborate
When a user initiates a logout, the user will be logged out from all applications in the current Identity provider login session.