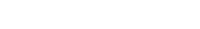SAML Assertion Validation
Introduction
To ease the process of SAML configuration, we have introduced a validator that verifies the SAML response and simplifies the debug process in the SSO login failure event directly within Prolaborate.
Prerequisites
- Prolaborate Version should be 5.2.0 and above.
- To validate the SAML response, the user should be a Prolaborate Admin.
How to validate the response?
In the User Login Audit view, the success and failure events of users logging into the application are captured. In the event of failure for Identity Provider User (SSO User), the response code generated is captured and an admin can validate the response directly from there.
Find the specific Identity Provider User then, Click on view under More Details.
Click on Menu > User Login Audit where login event of all user types is captured. To find the reason for failure of login of an Identity Provider User . Click on view under More Details..
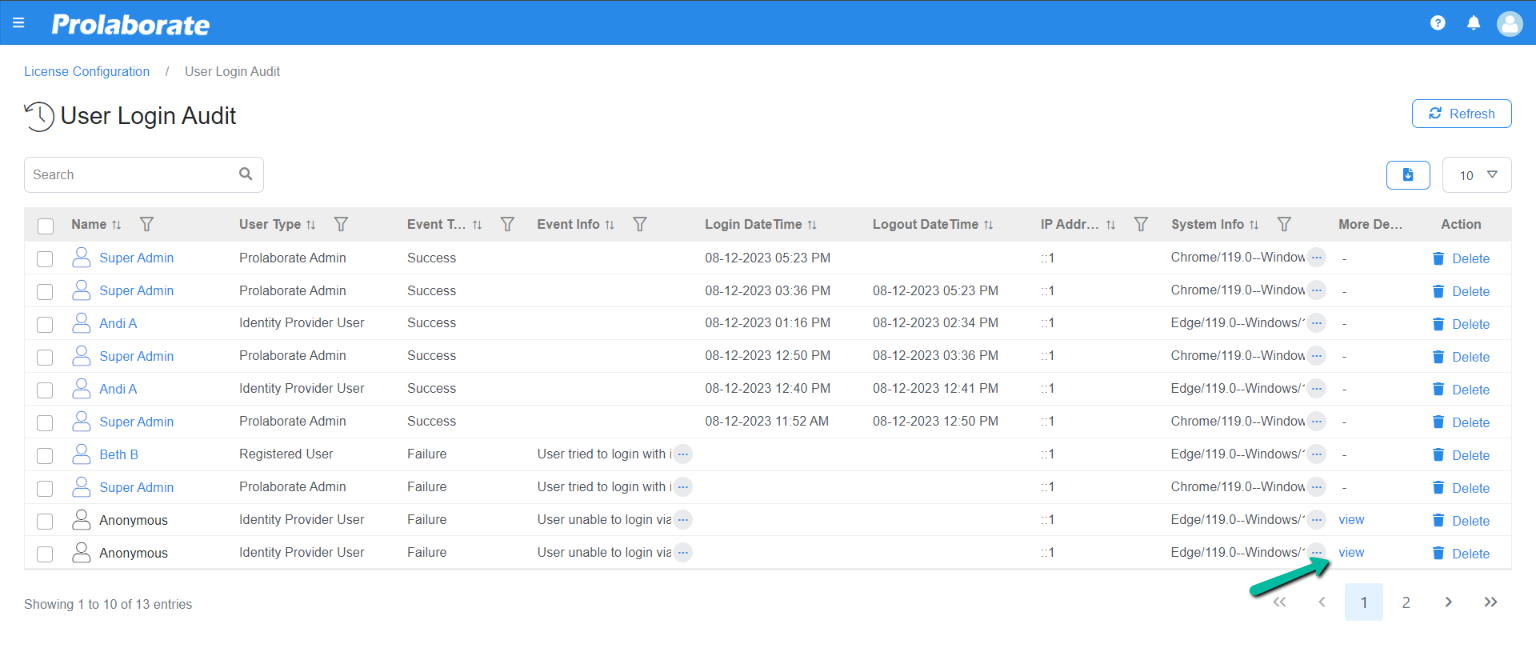
The response code generated is displayed in the popup window. Admin can click Validate Response which redirects to the SAML SSO Validator page for the validation process to initiate.
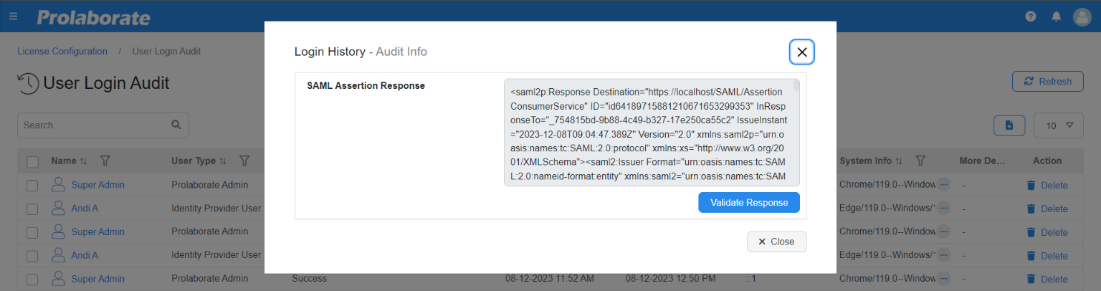
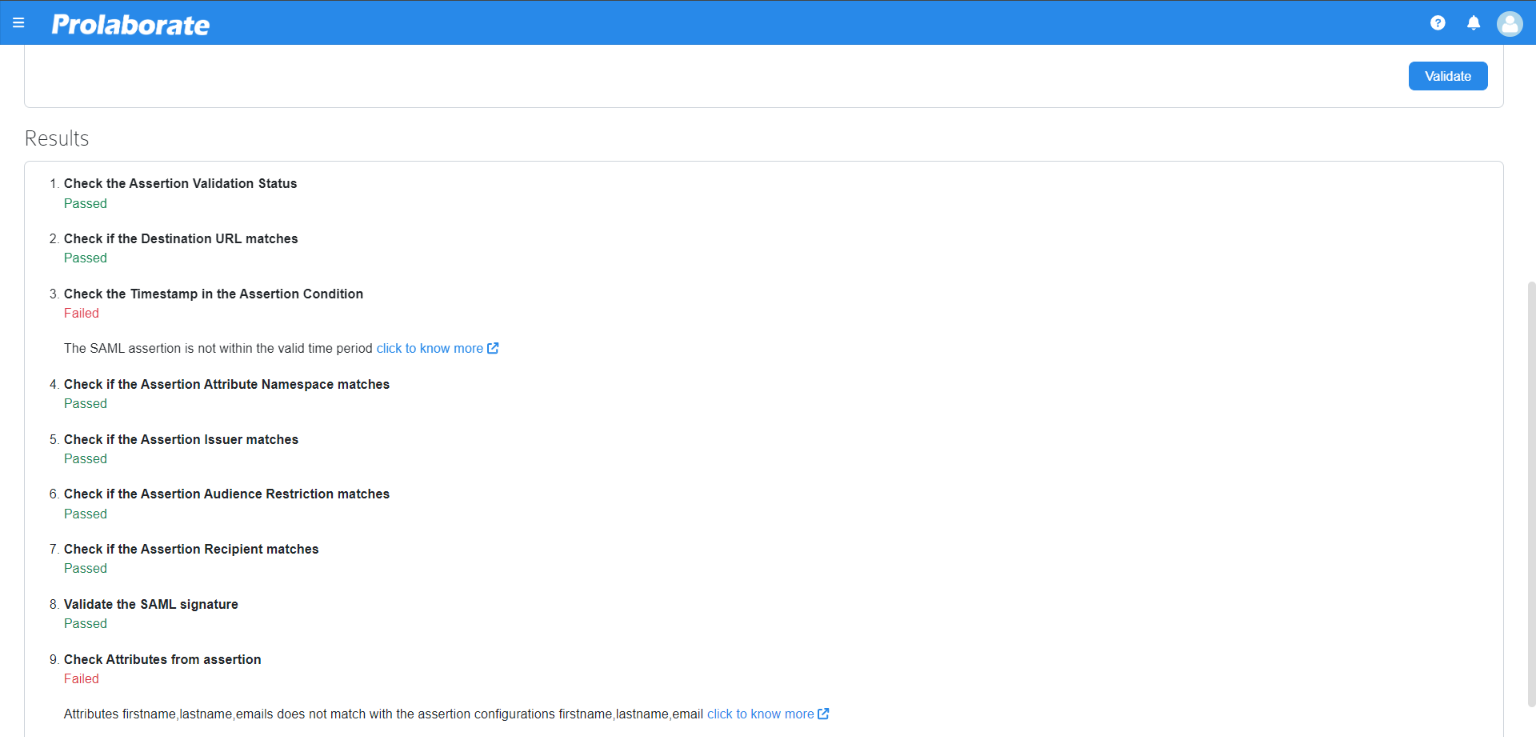
Once the validations are complete, the Results section shows the reason for the login failure.
Troubleshoot
Once the validation is completed, administrator will receive a set of results that causes the error. We have mentioned the type of error and the remediation below for each type of error.
1. Check the Assertion Validation Status
- Verify that the overall configuration meets the necessary requirements. This issue may arise if the configuration doesn’t align with conditions not covered on the below validation points.
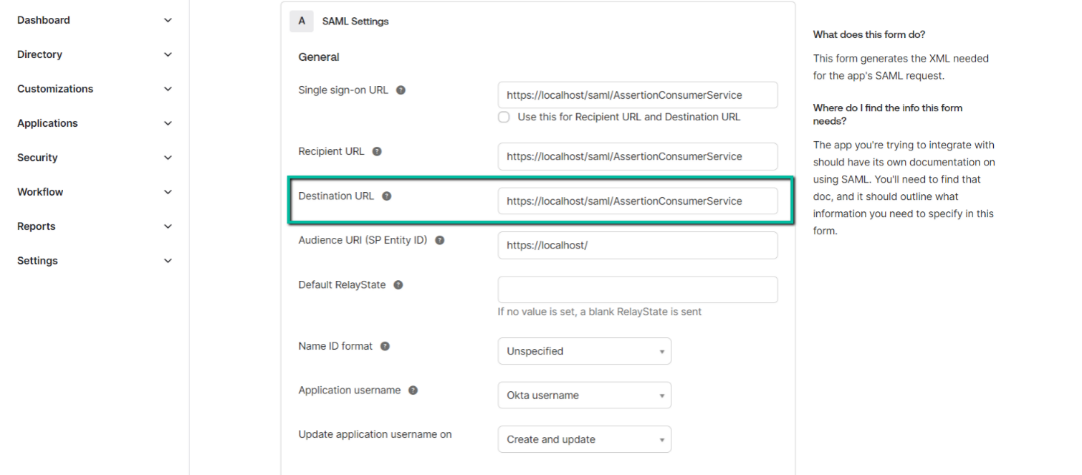
2. Check if the Destination URL matches
- Confirm if the Destination URL entered in the Identity Provider (IDP) matches with the Assertion Consumer URL under Service Provider Configuration in Prolaborate.
3. Check the Timestamp in the Assertion Condition
- If the system date is incorrect, you might encounter this issue. This usually happens if a user has mistakenly set an inaccurate date. Double-check and ensure your system date is accurately configured to avoid any potential disruptions.
4. Check if the Assertion Attribute Namespace matches
- Optimize your setup by confirming your configuration is aligned with SAML 2.0, the supported protocol exclusive to Prolaborate. Refer to the user guide for detailed instructions and insights on leveraging the benefits of SAML 2.0 within Prolaborate.
5. Check if the Assertion Issuer matches
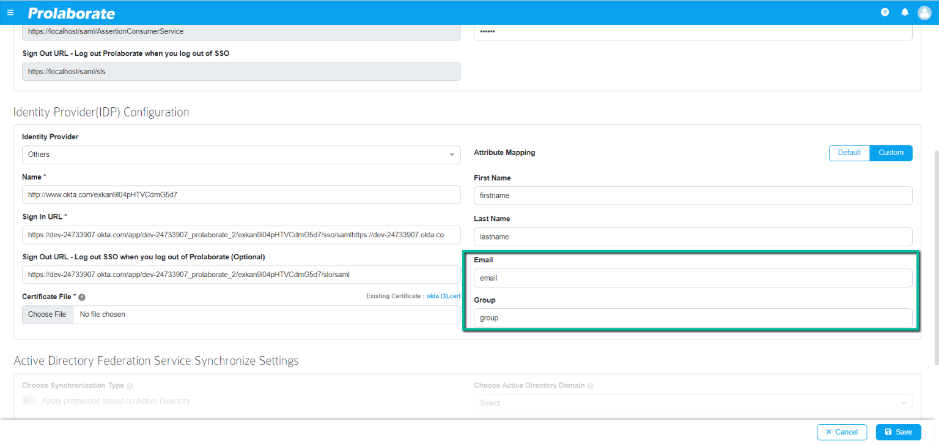
- Confirm if the Name entered under Identity Provider Configuration in Prolaborate matches with the SAML Issue.URL under Service Provider Configuration in Prolaborate.
6. Check if the Assertion Audience Restriction matches
- Ensure that the link copied from the Name under Service Provider (SP) section of Prolaborate and entered in the Identity Provider are correct.
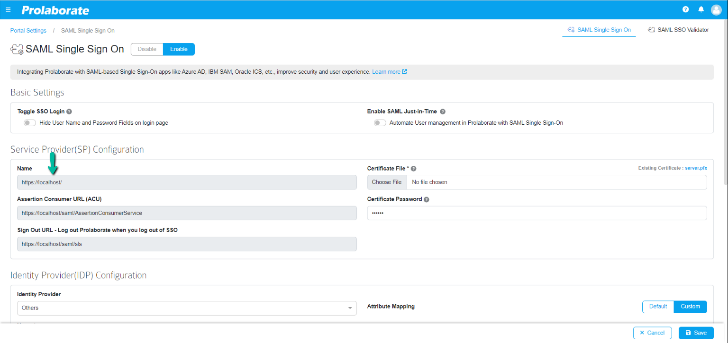
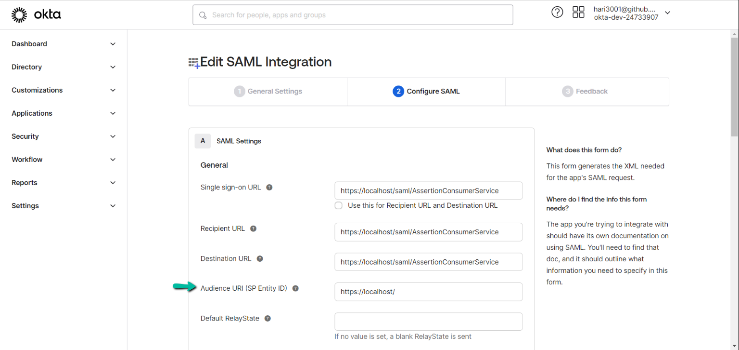
Above image is an example where we have used OKTA as IDP do demonstrate the configuration.
7. Check if the Assertion Recipient matches
- Check if the Recipient URL entered in the Identity Provider matches with the Assertion Consumer URL under Service Provider Configuration in Prolaborate.
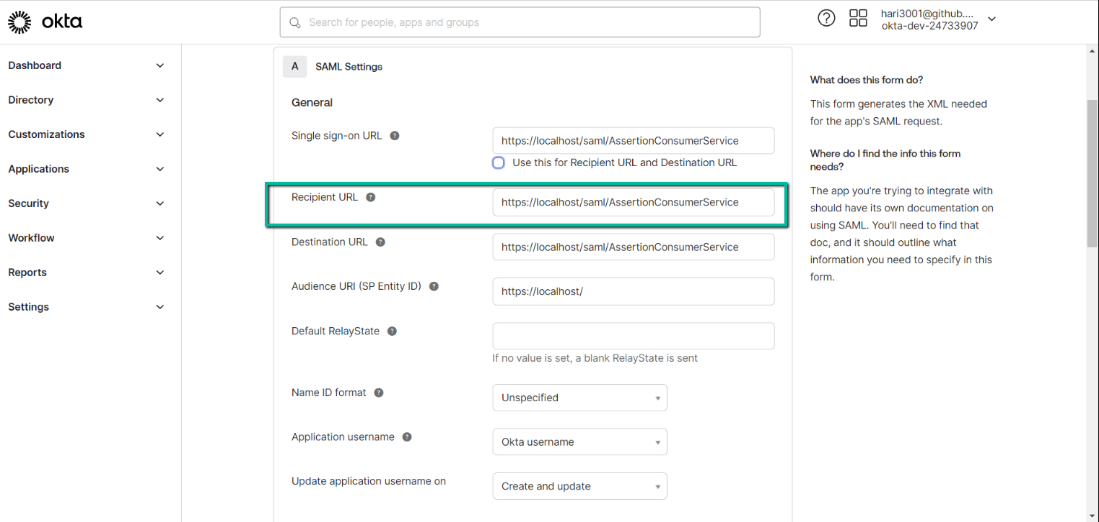
8. Validate the SAML signature
- Check if you’ve uploaded a valid (.cer) certificate.
9. Check Attributes from assertion
- Check that the email or group mapping you entered in the Attribute mapping is valid to ensure smooth validation. Refer to the user guide for step-by-step instructions on entering valid details.